SSH Port Forwarding - Port Tunnling Using Putty on Windows
Are you in a situation where you need to access a network or service that is only available on a remote machine, but you are unable to connect directly due to firewalls or other restrictions? One solution is to use SSH tunneling, also known as SSH port forwarding, to securely forward network traffic from one device to another using a Secure Shell (SSH) connection. In this blog post, we'll show you how to create an SSH tunnel in Windows using PuTTY, a popular SSH client for Windows.
Before you begin, you will need to have PuTTY installed on your local machine. You can download it from the official website (https://www.putty.org/).
To create an SSH tunnel in Windows using PuTTY:
-
Open PuTTY and enter the hostname or IP address of the remote machine in the "Host Name (or IP address)" field.
-
In the "Category" pane on the left, navigate to "Connection > SSH > Tunnels".
-
In the "Source port" field, enter the local port that you want to use for the tunnel. This is the port that you will use on your local machine to access the network or service on the remote machine.
-
In the "Destination" field, enter the hostname or IP address of the remote machine, followed by a colon and the port on the remote machine that you want to forward to. For example:
remotehost:80 -
Click the "Add" button to add the tunnel to the list.
-
In the "Category" pane, navigate to "Session" and enter a name for the connection in the "Saved Sessions" field. Then click the "Save" button to save the connection.
-
Click the "Open" button to establish the connection and create the tunnel.
-
When prompted, enter your username and password for the remote machine.
You should now be connected to the remote machine, and any traffic sent to the specified local port will be forwarded to the specified remote port on the remote machine.
For example, to forward traffic from port 8080 on your local machine to port 80 on a remote machine, you could use the following settings:
- Source port: 8080
- Destination: remotehost:80
This would allow you to access the web server running on the remote machine by visiting http://localhost:8080 on your local machine.
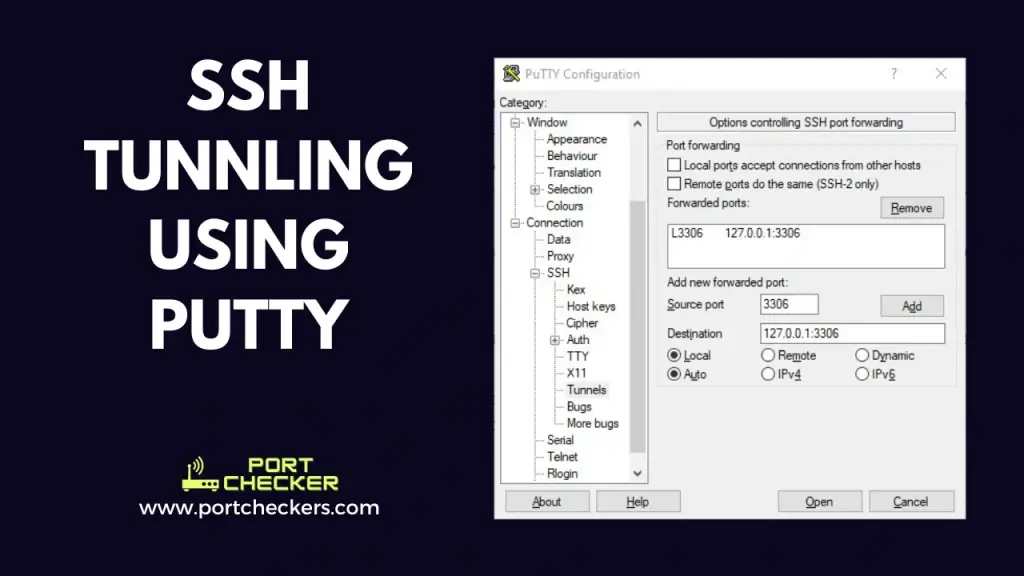
Accessing remote MySQL server which is not exposed to Firewall and Public IP
In this scenario we will configure Source port: 3306 and Destination: 127.0.0.1:3306 . This will create a tunnel to the
remote machine and will connect remotely hosted mysql using localhost or 127.0.0.1 and once the connectin is established you will be
able to access mysql on your local machine my connecting to 127.0.0.1 at port 3306 .
Note that you can also use PuTTY to create an SSH tunnel without connecting to a remote shell by enabling the "Don't start a shell or command at all" option in the "Connection > SSH > Tunnels" settings. This can be useful if you just want to use the tunnel and don't need to run any commands on the remote machine.
Some of the use cases of SSH tunneling / SSH port forwarding
There are many different use cases for SSH tunneling, also known as SSH port forwarding. Here are a few examples:
-
Bypassing firewalls: If you are unable to connect to a remote network or service due to a firewall, you can use SSH tunneling to bypass the firewall and securely connect to the network or service.
-
Securely accessing a remote network: SSH tunneling can be used to securely connect to a remote network, allowing you to access resources on the network as if you were physically connected to it. This can be especially useful if you need to access a network or service from a public or untrusted network, such as a coffee shop or airport.
-
Remote access to a private network: If you need to access resources on a private network from a remote location, you can use SSH tunneling to create a secure connection to the private network. This can be useful for remotely accessing servers, databases, or other resources on the private network.
-
Accessing resources on a network with NAT: If you are on a network that uses NAT (Network Address Translation), you may not be able to connect directly to resources on other networks. SSH tunneling can be used to bypass NAT and access resources on other networks.
-
Encrypting unencrypted protocols: SSH tunneling can be used to encrypt traffic for protocols that do not have built-in encryption, such as Telnet or VNC. This can help to improve the security of your connections and protect sensitive data.
Overall, SSH tunneling is a powerful tool that can be used in a variety of situations to securely connect to remote networks and access resources. In conclusion, SSH tunneling is a useful technique for securely accessing networks and services on remote machines, and PuTTY is a convenient tool for creating SSH tunnels in Windows. By following the steps outlined above, you can easily set up an SSH tunnel and start using it to access the resources you need.