Port Checker - Check Open Ports
The Port Checker tool can verify whether the ports of any internet-connected device are open or closed.
What Is a Port Checker and How Does It Work?
Port Checker is a free online tool that checks a remote computer or device's Internet connectivity. It can be used to check for open ports or to Ping a remote server. This tool is also useful for testing Port Forwarding settings.
The TCP Port Checker attempts to connect to the server and displays a success message on the screen if the connection is successful or if it receives a port open signal.
You can't use this tools to check local ports in your computer.. To run this test, your computer or network device must be directly connected to the internet, or a port must be forwarded to the system if connected via a router.
What are the Prerequisites for port testing?
- Checking ports is only possible if your computer is accessible via an public IP address.
- When you are inside a subnet it is only possible with port forwarding.
- Network access: You need access to the network where the port you want to test is located. This may require you to have physical access to the network, or you may need to remotely connect to the network using a VPN or other remote access tool.
- Knowledge of the target port: You need to know the port number or protocol of the port you want to test. This information is usually available in documentation or online resources.
- Firewall Access: Target port must be opened in Firewall.
Also, please note that in case you are testing open port for your local IP address i.e. if your Ip is similar to 192.168.1.xxx you are trying to check open port on internal IP and it is not going to work. If you are not sure about IP address and Port you shoud read more about [ Port Forwarding on Wikipedia ]
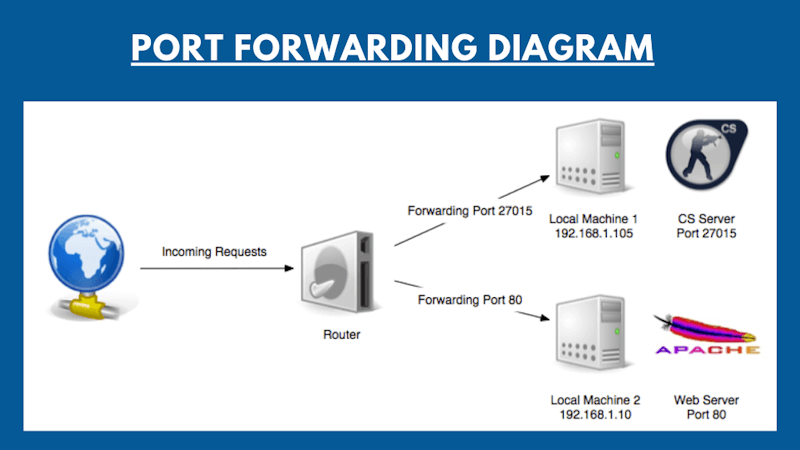
What is port forwarding?
Port Forwarding is a kind of special configuration on the router, which allows to redirect external requests (from the Internet) to computers or other devices on the local network. In fact it is a way to specify which local computer to send data and connection requests that arrive at a specific port on the router. We have three different ways we can do this:
- Faux-DMZ: DMZ stands for Demilitarized Zone , which is a kind of network security configuration in which all incoming requests are sent to a specific computer in the network.
- Port forwarding:
- UPnP port forwarding: It is similar to Port Forwarding but in this case forwarding setting is done by a computer software which is residing on the Network. A very common example in the scenario is UPnP port forwarding setup done by Skype. Skype conference call is actually performed this way.
Let's say you have Minecraft Game Server or Apache Web server connected to the Internet via a router. All computers connected to the same router are on the same network, so will be able to connect to the server. However, outside of the Internet, connect to your server without port forwarding will not work. You must port forward Port 25565 for Minecraft and 80 for Apache to be accesible from Public internet. If your computer is connected to the Internet directly (without a router / router), then port forwarding is not required. All your open ports must be accessible from the Internet (of course, if you have a dedicated IP and these are accessible through your computer's Firewall ).
How to Test My Firewall
In case you have set up DMZ host and you want to test whether your firewall is effective of not, same can be verified by port checker tool. Use your public ip and test the ports which you have configured to block from your firewall.
What are ports? What are they used for?
In addition to these physical ports, computers also have virtual ports, which are used to communicate with other devices or services over a network using specific protocols. These virtual ports are identified by a port number, which is a unique number assigned to each type of service or protocol. For example, port 80 is used for HTTP (Hypertext Transfer Protocol), the protocol used to transfer web pages over the internet.
Ports are identified by numbers from 0 to 65535, inclusive. Any other port can not be opened, respectively, and check too. This limitation TCP / IP protocol.
It is worth noting that the client program should always know the port to which it needs to connect to a remote server or another network device. For this reason, the most popular protocols reserved ports in the range from 0 to 1023.
For example, carrying out surfing on the Internet, your browser connects to port 80 on a remote server that hosts the site.
In response, the browser receives a set of data and code that downloads and displays a web page.
If you are not sure about the port numbers you do a port number lookup from standard database.
What are the different port numbers?
Out of the so many port numbers here are a few which are most frequently used.
| Protocol | Port | Description |
|---|---|---|
| FTP | 21 | File Transfer Protocol - File Transfer Protocol. Port for commands. |
| SSH | 22 | Secure SHell - "secure shell". Remote Management Protocol operating system. |
| Telnet | 23 | TerminaL Network. Protocol implementation text interface over the network. |
| SMTP | 25 | Simple Mail Transfer Protocol - Simple Mail Transfer Protocol. |
| WHOIS | 43 | "Who is". Protocol obtaining the registration of ownership of domain names and IP addresses |
| DNS | 53 | Domain Name System - Domain Name System. |
| DHCP | 67 | Dynamic Host Configuration Protocol - Dynamic Host Configuration Protocol. Dynamic IP |
| TFTP | 69 | Trivial File Transfer Protocol - a simple file transfer protocol. |
| HTTP / Web | 80 | HyperText Transfer Protocol - hypertext transfer protocol. |
| POP3 | 110 | Post Office Protocol Version 3 - receive e-mail protocol, version 3 |
| SFTP | 115 | SSH File Transfer Protocol. Secure data transmission protocol. |
| IMAP | 143 | Internet Message Access Protocol. Application-level protocol for accessing e-mail. |
| SNMP | 161 | Simple Network Management Protocol - Simple Network Management Protocol. Device Management. |
| HTTPS | 443 | HyperText Transfer Protocol Secure) - protocol HTTP, which supports encryption. |
| LPD | 515 | Line Printer Daemon. Remote printing protocol on the printer. |
| IMAP SSL | 993 | Protocol IMAP, supports SSL encryption. |
| POP3 SSL | 995 | POP3 protocol supports SSL encryption. |
| SOCKS | 1080 | SOCKet Secure. Receiving protocol secure anonymous access. |
| Proxy | 3128 | Currently the port often used proxies. |
| MySql | 3306 | Mysql database |
| RDP | 3389 | Remote Desktop Protocol - Remote Desktop for Windows. |
| PostgreSql | 5432 | Postgres Database |
| VNC | 5900 | Virtual Network Computing - a system of remote access to the desktop computer. |
| TeamViewer | 5938 | TeamViewer - Remote control system for ensuring your computer and data exchange. |
| HTTP / Web | 8080 | Alternate port for the HTTP protocol. Sometimes used proxies. |
| Helium | 44158 | Helium Miner Port |
| Minecraft | 25565 | Minecraft Server Port |
Command to test open ports in MAC, Windows or Linux computers
If you using a Windows or Linux machine, you can easily find open ports or ports which are in use using below commands :
Windows : Start → "cmd" → Run as Administrator → "netstat -bn"
Linux : a In the terminal, run the command: "ss -tln"
MAC : lsof -iTCP -sTCP:LISTEN -n -P
How to close an open port?
First of all it is necessary to remove the cause - a running program or service that opened the port; it is necessary to close / stop. If the open port reason is not clear - Antivirus scan your computer, delete the extra port forwarding rules on the router and set the advanced firewall (Firewall).
Port Checker - Frequently Asked Questions(FAQ)